Steve Jobs’ genius may prove irreplaceable at Apple, according to IHS iSuppli, which recently polled the opinions of its analysts, asking the question: "Can Apple Stay on Top Without Jobs?"
The experts disagree on how much Apple's stunning successes have depended on Jobs’ skills--and even which skills were most important. Consequently, IHS iSuppli turned to the hard facts in an attempt to trace the company's success to its source. The most important factual explanation for Apple's successes, according to senior analyst Wayne Lam, is Apple's margins.
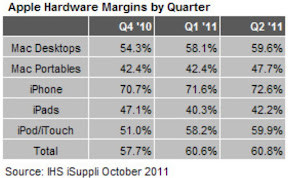
According to Lam, Apple's highest-volume product--the iPhone--enjoys hardware margins in excess of 70 percent. This makes Apple the industry's top money-maker in terms of market capitalization, according to Lam, who claims that Apple now has "more cash reserves than the U.S. Treasury."
"Apple’s iPhone product line has historically enjoyed very high hardware margins [of 60 to 70 percent]. In contrast, other leading smartphone brands typically get hardware margins of 50 percent or less," Lam said. "Another way of looking at this issue is that Apple's iPhone has consistently had the highest average selling price on the market today--around $645 while their competitors hover at around $400.”
According to Lam, Apple's high margins can be directly traced to Jobs' "laserlike focus," which enabled Apple to envision a clear path to success for new products. And once launched, Jobs did not allow naysayers to divert Apple's course, but saw product development efforts through to the end.
"Jobs didn’t care about quarterly reports, and he didn’t care what critics and the media said," noted Lee Ratliff, principal analyst, broadband and digital home for IHS. "All he cared about was implementing his vision. The force of his personality in this regard was enormous."
For instance, Apple did not invent the mouse and icon (that was done at Xerox Parc). However, Jobs did reinvent the graphical user interface that employed them for the Mac, then repeated that same model-for-success for the iPod, iPhone and iPad.
"Apple [took] all these products to a new level by reinventing how people interact with them," said Bob Braverman, senior director, communications and consumer electronics, at IHS. "This is entirely because of the visionary way in which Steve Jobs saw these markets and their usage models."
But can Apple maintain that methodology without Jobs? The past is littered with the remains of now-defunct companies with seminal visions, but not the wherewithal to sustain once the visionary leadership was gone. However, there are also success stories like Ford Motor Company that show it is possible to instill the founder’s personality into a corporate persona.
"Jobs has been compared to Thomas Edison and Henry Ford," said Dale Ford, senior vice president, electronics market intelligence for IHS. "These men were able to carry on their vision and legacy because the institutions they established lasted after their deaths. The question now is whether Apple has learned enough from Jobs that it can continue on with its success--like Ford Motor Co. did after the death of Henry Ford."
IHS claims the jury is still out, and will remain out for many years as Apple struggles to maintain its phenomenal margins against a sea of competitors, intent on clipping its wings.
"Without Jobs at the helm, Apple’s massive margins have got to wane at some point," said Braverman.
Further Reading